A firewall can be hardware or software that controls a device’s secure in-flow and out-flow of data. It monitors network traffic and serves as a firewall between trusted and untrusted networks. Firewalls, particularly Next-Generation Firewalls, are designed to protect against malware and application-layer attacks. When you use a firewall as part of your security infrastructure, you configure your network with specific policies that allow or block incoming and outgoing traffic.
What is a Firewall in a Computer Network ?
A firewall is a hardware or software-based network security device that monitors all incoming and outgoing traffic and accepts, rejects or drops that traffic based on a defined set of security rules. A firewall creates a barrier between secure internal networks and untrusted networks like the Internet.
A firewall is analogous to a sentry stationed outside the home of an important person (such as the president of India). This sentry generally keeps an eye on and physically checks everyone who comes and goes from the house. If the sentry suspects that a person attempting to enter the president’s residence is carrying a knife, the person will be denied entry. Similarly, the sentry may still refuse entry even if a person does not possess any prohibited items but appears suspicious. 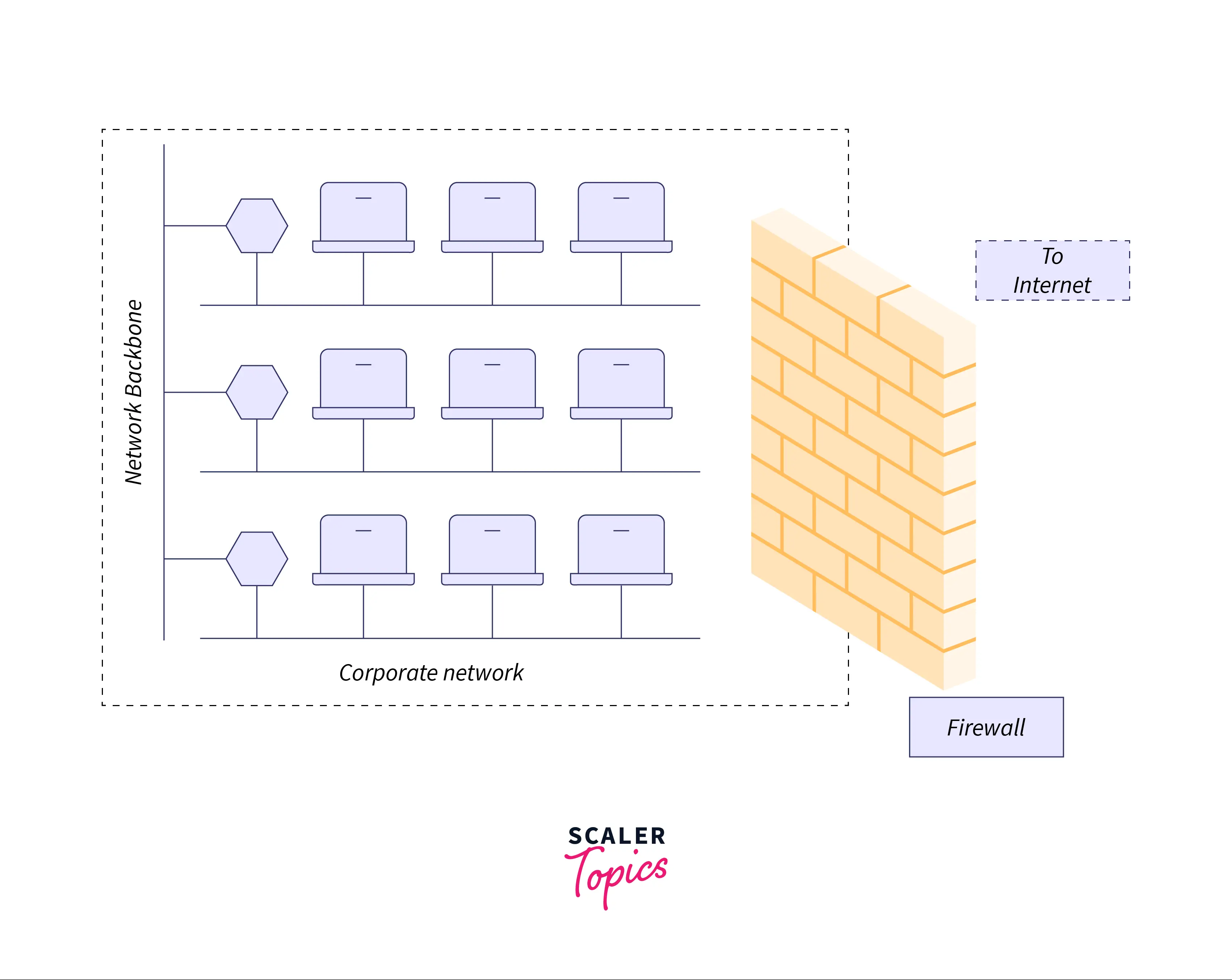
A firewall is similar to a sentry. It protects a corporate network by acting as a barrier between the network and the outside world. The traffic between the network and the Internet must pass through the firewall. The firewall determines whether traffic can be allowed to flow or must be stopped.
History and Need for Firewall
The term “Firewall” actually referred to a structure designed to contain a fire within a line of adjacent buildings. The firewall was not recognized as computer terminology until the late 1980s. Network firewalls have evolved to address a variety of security threats. Firewalls will continue to be important in organizations and society. So, let’s take a look at the history of firewalls.
In 1993, Gil Shwed from Check Point Technologies introduced the first stateful inspection firewall. It was known as FireWall-1. Netscreen introduced its purpose-built firewall, ‘Appliance’, in 2000. It gained popularity and rapid adoption within enterprises due to increased internet speed, lower latency, and high throughput at a lower cost.
A new strategy for firewall implementation was introduced at the turn of the century in the middle of 2010. Palo Alto Networks introduced the “Next-Generation Firewalls”. These firewalls have several built-in functions and capabilities, including Hybrid Cloud Support, Network Threat Prevention, Application, and Identity-Based Control, Scalable Performance, and others. When it comes to network security, they are regarded as the first line of defense.
Organizational Internet connectivity is no longer optional. However, access to the Internet benefits the organization. It also allows the outside world to interact with the organization’s internal network. This poses a risk to the organization. A firewall is required to protect the internal network from unauthorized traffic.
Generation of Firewalls in Computer Networks
First Generation : Packet Filtering Firewall
A packet filtering firewall controls network access by monitoring outgoing and incoming packets and allowing them to pass or block based on source and destination IP addresses, protocols, and ports. It examines data at the transport protocol layer (but mainly uses the first three layers). These packet filters have no way of knowing whether a packet is part of an existing traffic stream. But it has the authority to allow or deny packets based on their unique packet headers.
Second Generation : Stateful Inspection Firewall
Stateful firewalls can determine a packet’s connection state, making them more efficient than packet filtering firewalls. It keeps track of the status of network connections, such as TCP streams, that pass through it. Filtering decisions would be based not only on defined rules but also on packet history in the state table.
Third Generation : Application Layer Firewall
Any OSI(Open System Interconnected) layer, up to the application layer, can be inspected and filtered by an application layer firewall. It can block specific content and detect when certain applications and protocols (such as HTTP and FTP) are being misused.
Next-Generation Firewalls
These firewalls are being deployed to prevent modern security breaches such as advanced malware attacks and application-layer attacks. Application Inspection, Deep Packet Inspection, SSL/SSH inspection, and other features protect the network from modern threats. Next-Generation firewalls inspect packets at the application level of the TCP/IP stack and can identify and enforce security policies based on the type of application, such as Skype or Facebook.
Working on Firewall
A firewall system analyses network traffic based on pre-defined rules. It then filters the traffic to prevent it from coming from untrustworthy or suspicious sources. It only allows incoming traffic that has been configured to accept it. Firewalls typically intercept network traffic at a computer’s entry point, referred to as a port. Firewalls accomplish this by allowing or blocking specific data packets (communication units transferred over a digital network) based on pre-defined security rules. Incoming traffic is only permitted from trusted IP addresses or sources. The diagram given below can easily explain the working of a firewall. 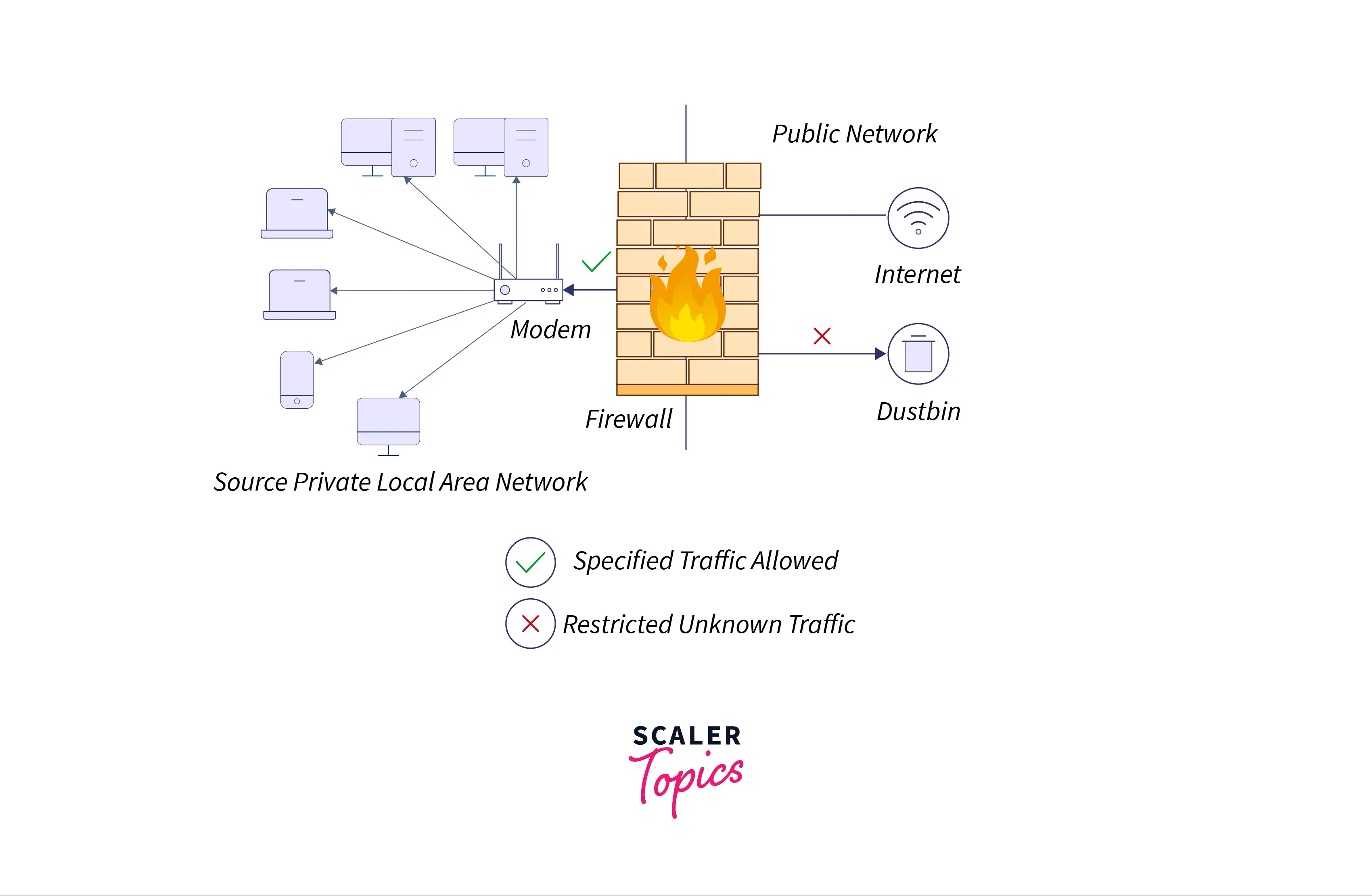
Types of Firewalls in Computer Networks
Firewalls are classified into three types based on their structure : software firewalls, hardware firewalls, or both.
- A hardware firewall is a physical network security device that connects a computer network to a gateway. As an example, consider a broadband router. A hardware firewall is also known as an Appliance Firewall.
- A software firewall is a simple program that is installed on a computer and works by using port numbers and other software that is already installed. A Host Firewall is another name for this type of firewall.
There are numerous other types of firewalls based on their features and level of security. 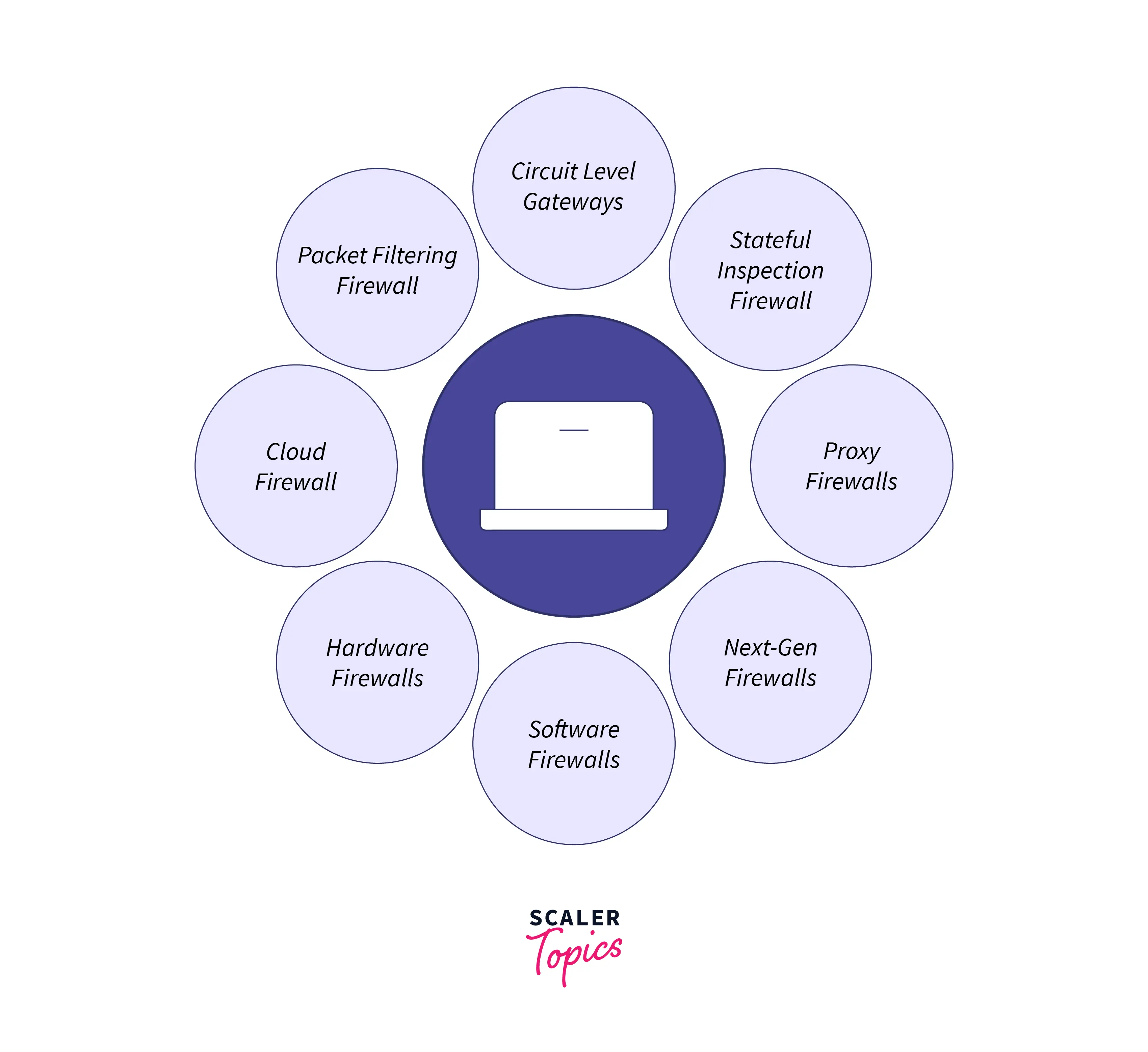
Packet-Filtering Firewall
The most basic type of firewall is a packet filtering firewall. It functions as a management program, monitoring network traffic and filtering incoming packets based on security rules that have been configured. Packet firewalls are designed to block network traffic IP protocols, a port number, and an IP address if a data packet does not match the established rule set.
Circuit-Level Gateways
A circuit-level gateway is another more straightforward sort of firewall that can be readily set to accept or block traffic without using a lot of processing resources. These firewalls typically function at the OSI model’s session level by confirming TCP (Transmission Control Protocol) connections and sessions.
Circuit-level gates are intended to guarantee the security of the established sessions. These firewalls examine information about transmission, just like packet-filtering firewalls, but they do not look for real data. As a result, if a piece of data has malware but uses the proper TCP connection, the gateway will let it through.
Application-Level Gateways
A firewall at the application layer can examine and filter packets at any OSI layer, including the application layer. It can prohibit particular types of information and identify when applications and protocols (such as HTTP and FTP) are being abused. In other words, hosts that operate proxy servers are Application layer firewalls. Each packet must pass through the proxy in a proxy firewall to establish a direct connection between either side of the firewall. Depending on previously established restrictions, it might permit or prevent traffic.
Stateful Multi-layer Inspection (SMLI) Firewalls
Stateful multi-layer inspection firewalls (SMLI firewalls) are preferable to packet-filtering firewalls or circuit-level gateways because they provide both packet inspection technology and TCP handshake verification. These firewalls also monitor the status of connections that have already been made.
Simply, the SMLI firewall creates a database whenever a user starts a connection and requests data (state table). Data about sessions, including source IP address, port number, destination IP address, destination port number, etc., is kept in a database. Each session’s state table contains connection information. These firewalls generate security rules to enable anticipated traffic using stateful inspection technologies.
Next-Generation Firewalls (NGFW)
NGFW offers more security than stateful inspection and packet filtering firewalls. NGFW monitors the complete data transaction, including packet headers, packet contents, and sources, in contrast to traditional firewalls. NGFWs are created in a way that enables them to counteract more complex and developing security risks, including malware assaults, external threats, and intrusions in advance.
Threat-focused NGFW
All the characteristics of a standard NGFW are present in threat-focused NGFW. They additionally offer enhanced threat detection and remediation. These firewalls can respond to threats quickly. Threat-focused NGFW sets security rules and policies using intelligent security automation, further enhancing the security of the whole defensive system. These firewalls also continuously detect questionable activity using retroactive security systems.
Network Address Translation (NAT) Firewalls
Network address translation (NAT) firewalls are primarily intended to access Internet traffic while blocking all unauthorized connections. These firewalls usually hide our devices’ IP addresses, making them safe from attackers. When multiple devices connect to the Internet, NAT firewalls generate a unique IP address and obscure the IP addresses of individual devices. As a result, all devices share a single IP address. NAT firewalls protect independent network addresses from attackers scanning a network for IP addresses. As a result, suspicious activities and attacks are better protected.
Cloud Firewalls
When a firewall is built using a cloud solution, it is referred to as a cloud firewall or FaaS. (firewall-as-service). Third-party vendors typically maintain and operate cloud firewalls on the Internet. This type of firewall is comparable to a proxy firewall. Scalability is the most significant advantage of cloud firewalls. Because cloud firewalls do not require physical resources, they can be easily scaled to meet the organization’s needs. If demand grows, more capacity can be added to the cloud server to handle the increased traffic load.
Unified Threat Management (UTM) Firewalls
The UTM firewalls are a unique class of devices that combine stateful inspection firewall functionality with intrusion detection and prevention capabilities. These firewalls are made to be simple and simple to use. Numerous more services, such as cloud management, can be added to these firewalls.
Functions of Firewall
- As a Network Security Post :
A firewall serves as a security checkpoint and inspection point for all traffic entering or leaving the network. The firewall will attempt to filter all incoming traffic in line with the established security every time it occurs. - Prevent unauthorized disclosure of sensitive information :
To ensure that every data flow is under the control of a firewall, several firewalls are installed for File Transfer Protocol (FTP) for this single function. A firewall is helpful in this situation to stop network users from transferring priceless secret files to third parties. - Prevent Modification of Other Party Data :
In organizations, information such as financial statement information, product specifications, and other business information that, if made public, would be detrimental to the business. The firewall prevents the modification of these data so that they remain safe. - Record User Activity :
Network users must pass through a firewall each time they access data, which records the request as documentation (log files) that can later be accessed to create security systems. The firewall may read log data and provide usage statistics for the network.
Limitations of Firewall
- Apart from the services and security the firewall provides, it has some limitations.
- Firewalls are subject to internal threats or attacks since they cannot prevent users from accessing malicious websites.
- Firewalls cannot stop password misuse.
- Firewalls cannot prevent attackers using modems from dialing into or out of the internal network.
- Firewalls cannot protect a system that has already been infected.
- If security rules are configured incorrectly, firewalls cannot protect.
Advantages of Firewall
- A firewall detects hackers and remote access.
- It provides better security and network monitoring features.
- It protects from trojans.
- A firewall ensures better privacy and security.
Disadvantages of Firewall
- Installing a firewall could be expensive, depending on how sophisticated it needs to be.
- A firewall has some limitations, such as its inability to prevent virus and malware attacks, which would require separate applications at the individual system level.
- Need for professionals to manage.
Conclusion
- A firewall is a hardware/software-based network security device that monitors all incoming and outgoing traffic and accepts, rejects, or drops that traffic based on a defined set of security rules.
- A hardware firewall is a physical device that connects a computer network to a gateway.
- A software firewall is a simple program that is installed on a computer and works by using port numbers and other software that is already installed.
- There are generally nine types of firewalls based on their features and level of security.
- The important functions of the firewall are :
- Prevent unauthorized disclosure of sensitive information
- Prevent Modification of Other Party Data
- Record User Activity
- Act as a Network Security Post
- There are 4 four generations of Firewalls till now, including the latest Next Generation Firewall.
