A protocol hierarchy in computer networks refers to the organization and arrangement of networking protocols in a layered structure. This layered approach helps in achieving interoperability, modularity, and ease of implementation and maintenance within complex network systems. The most well-known protocol hierarchy is the OSI (Open Systems Interconnection) model, which consists of seven layers. You should be familiar with the OSI Model to better understand protocol hierarchies in computer networks.
Protocol
Protocols are a set of rules and agreements that computers use to communicate with each other over a network. Just like how people need to follow certain rules to have a conversation, computers also follow protocols to have effective communication.
Protocol Hierarchies
A protocol hierarchy in computer networking refers to the organization and arrangement of network communication protocols in a layered structure. This layered approach provides a systematic way to design, implement, and manage network communication, making it easier to understand and maintain complex systems. The most well-known example of a protocol hierarchy is the OSI (Open Systems Interconnection) model, which consists of seven layers.
Here’s a brief overview of the layers in the OSI model:
- Physical Layer: This layer deals with the physical connection between devices. It defines the electrical, mechanical, and functional aspects of the hardware, including cables, switches, and network interfaces.
- Data Link Layer: This layer is responsible for establishing a reliable link between two directly connected nodes, ensuring data integrity and error detection. It is often divided into two sublayers: Logical Link Control (LLC) and Media Access Control (MAC).
- Network Layer: The network layer is responsible for addressing, routing, and forwarding data packets between devices on different networks. It handles logical addressing (like IP addresses) and determines the best path for data to travel.
- Transport Layer: This layer ensures end-to-end communication, managing data segmentation, flow control, and error correction.
- Session Layer: The session layer establishes, manages, and terminates communication sessions between applications. It also handles synchronization and recovery in case of failures.
- Presentation Layer: This layer is responsible for data translation, encryption, compression, and other transformations to ensure that data from the application layer of one system can be understood by the application layer of another.
- Application Layer: The topmost layer is where user applications and network services directly interact. This layer defines protocols and services that applications use to communicate over the network.
Example
The picture shows a network with five parts that help Host 1 and Host 2 talk to each other. There are lines that look dotted to show where the parts on one side talk to the same parts on the other side. And there are solid lines that show how the parts next to each other are connected. These lines stand for real connections between the parts.
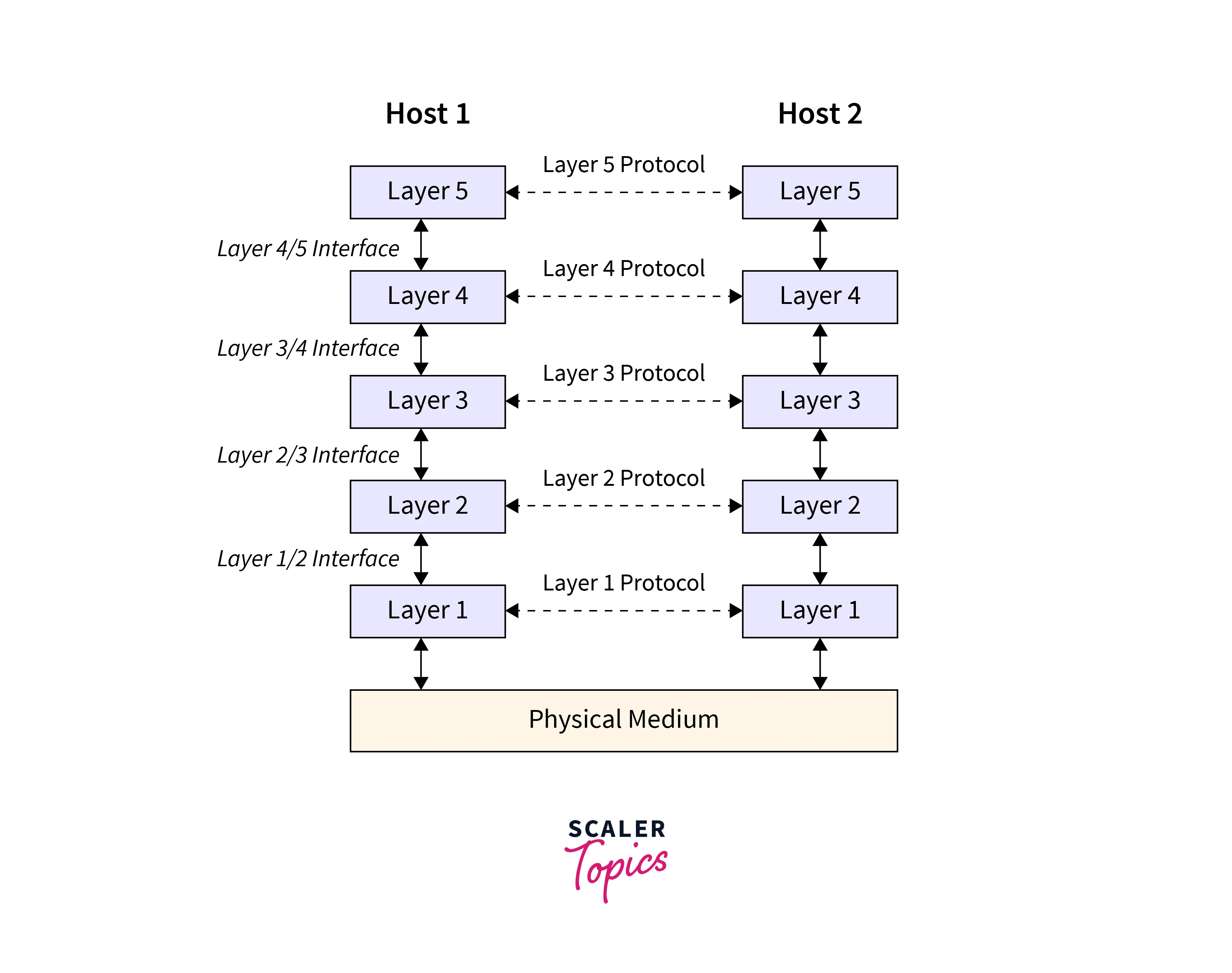
When the two hosts talk, they use different layers that are like buddies and have their own rules. Each layer talks to the one next to it through something called an interface, explaining how the lower part helps the upper part.
Advantages
- Network hierarchies, seen in models like OSI or TCP/IP, offer several advantages for efficient network design and management.
- Modular layers simplify complex functionalities, aiding development and troubleshooting.
- Troubleshooting is streamlined due to distinct layer separation, accelerating issue identification and resolution.
- Upgradability is enhanced as individual layers can be updated without disrupting the entire network.
- Standardized protocols ensure compatibility and security measures can be applied at specific layers.
Disadvantages
While network hierarchies offer numerous benefits, they also come with certain disadvantages that warrant consideration:
- The layering approach can lead to increased complexity in larger networks, as interactions between layers may become intricate and difficult to manage.
- They might not be flexible enough to handle new technologies or changes.
- They rely on established rules, potentially limiting new ideas and tech.
- Implementing and maintaining protocol hierarchies can be expensive due to specialized knowledge and equipment requirements.
- Updates or changes to one layer can have ripple effects across other layers, making maintenance more intricate and time-consuming.
Conclusion
- A protocol hierarchy in computer networks refers to the organization and arrangement of networking protocols in a layered structure
- Protocol hierarchies structure network design and communication for efficiency.
- A protocol hierarchy in computer networking refers to the organization and arrangement of network communication protocols in a layered structure.
- The OSI model serves as a foundational framework for understanding and implementing network communication protocols.
- Standardized protocols facilitate interoperability among diverse devices.